Create a key and add it to GCP
Your VM authenticates with other components through encrypted key pairs. Before you can connect to your VM from outside your cloud console, you must create and associate a key that identifies you.
You can manage your keys on GCP in one of two ways: you can use the OS Login Google service, or you can manage keys manually in the project metadata manually.
caution
Techwriting.io strongly recommends following Google's advice and using OS Login for production servers.
Perform the following steps to create a key pair and manually add a key to a GCP Project:
Generate an RSA key pair, these examples use the default name:
ssh-keygen -t rsaThis creates a public/private key pair, named "id_rsa" and places it in a hidden key directory on your computer.
Change directories to your key directory:
cd ~/.sshUsing a text editor, copy the public key contents from "id_rsa.pub":
atom id_rsa.pubNavigate to the compute engine page of your GCP console:
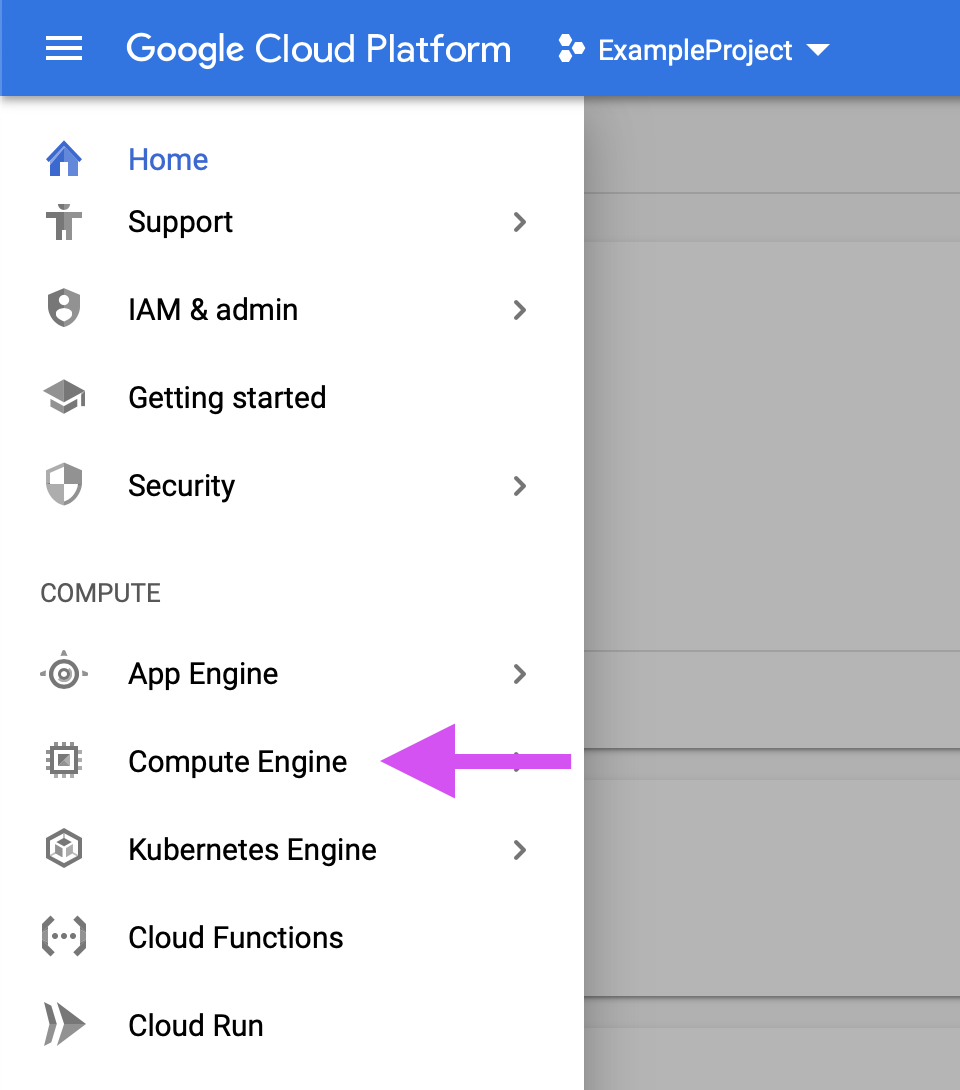
Select Metadata from the navigation bar on the left side of the screen:
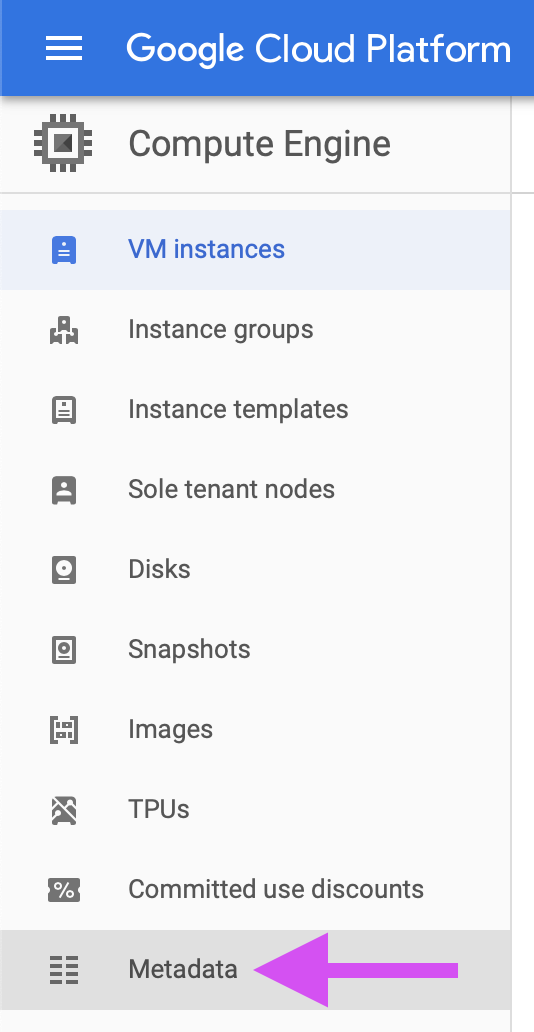
Select SSH Keys, then select the Edit button:
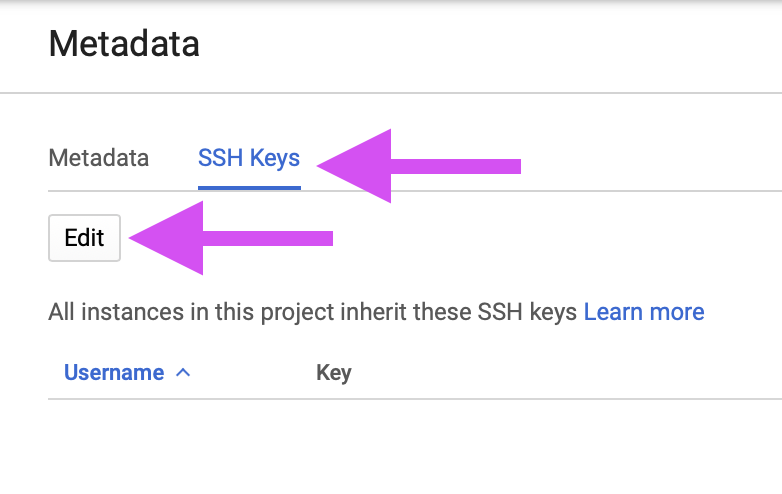
Select + Add item:
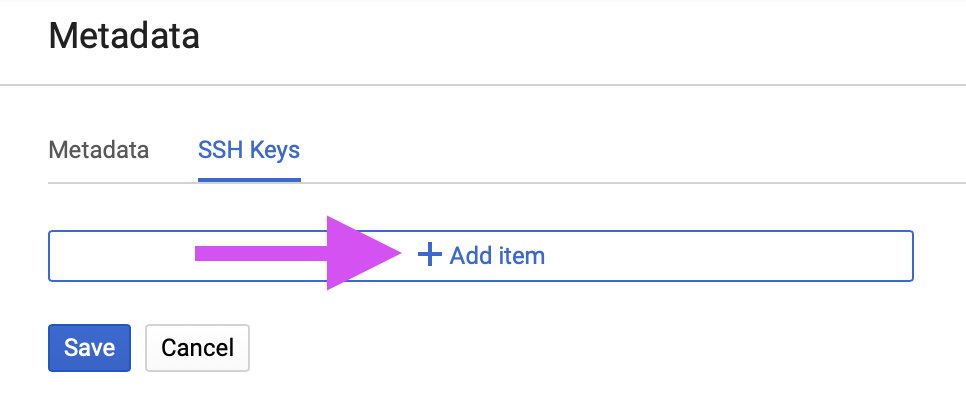
Paste your public key into the key text field in the Google Cloud console:
caution
This process manually assigns fixed key access. Techwriting.io strongly recommends rotating your keys on a planned interval as part of your security policies.
Ensure your public key was properly added by connecting to your VM using secure shell (SSH):
ssh username@serverIP
note
Citation note: I referenced the linked Google production documentation when I wrote this page, specifically the articles: OS Login and Managing SSH keys in metadata. In production doc, I would simply link to this documentation. However, this is a writing exercise, and I've documented my own steps for sample purposes.